
The Right to Be Forgotten: Understanding Data Privacy and Erasure
This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
Discover the latest insights, tutorials and expert analysis on cloud computing, serverless architecture and modern technology solutions.
Stay updated with the latest trends and insights in cloud computing technology

This article comprehensively explores the "Right to Be Forgotten," a critical aspect of data privacy laws, detailing its origins, legal frameworks, an...
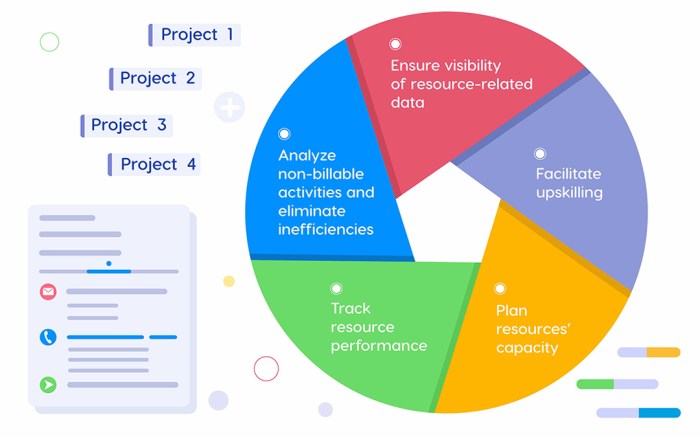
This comprehensive guide provides a detailed exploration of techniques to significantly reduce Docker image sizes, covering strategies from image buil...
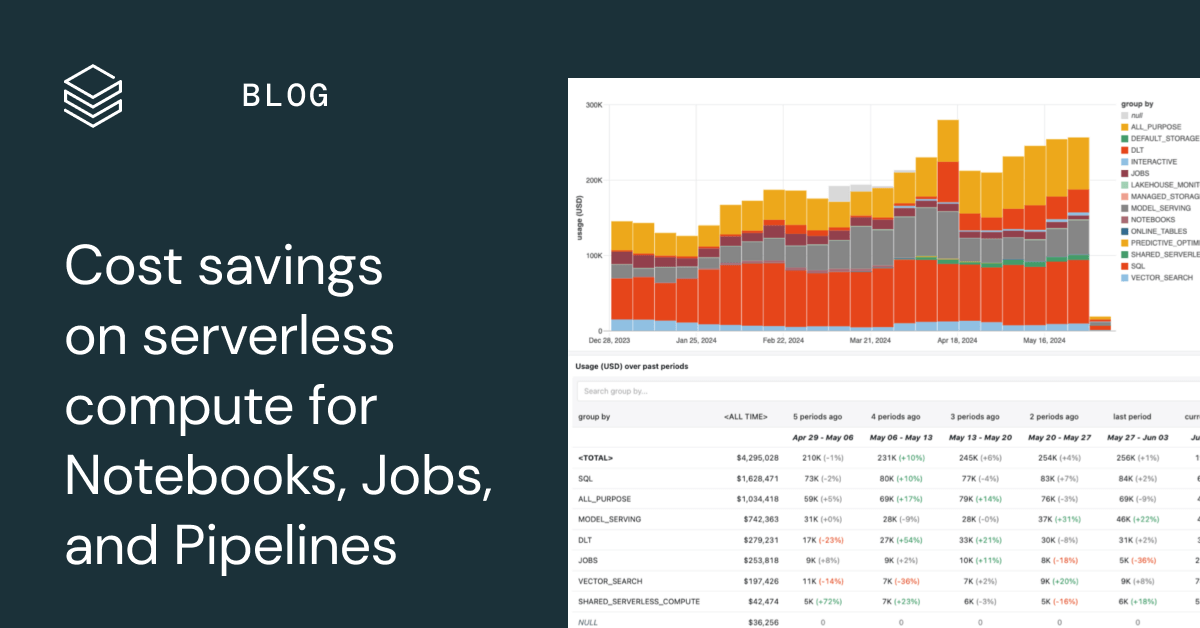
This comprehensive guide delves into the critical aspects of forecasting and managing serverless costs, providing actionable strategies for optimizing...

The digital world is constantly evolving, and staying informed about the latest security threats and vulnerabilities is crucial for both individuals a...
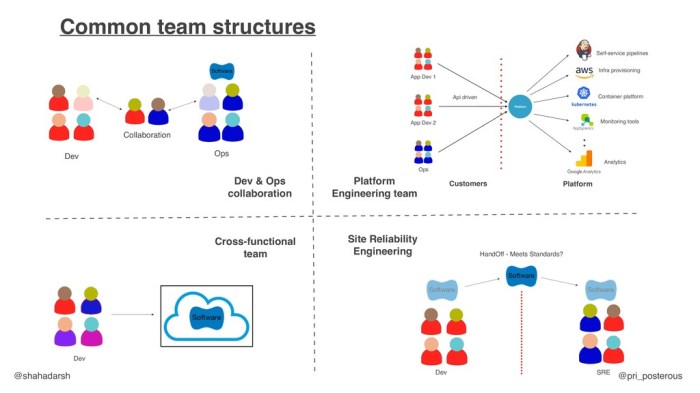
Platform engineering teams are vital in modern software development, providing the infrastructure and tools that streamline the entire development lif...

This comprehensive guide provides a deep dive into analyzing your cloud billing data, equipping you with the knowledge to understand cost fundamentals...
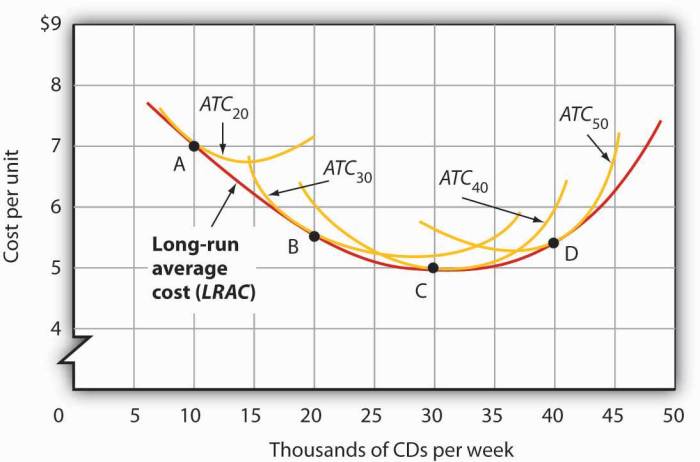
Navigating the cloud's vast storage landscape can be daunting, but understanding its associated costs is crucial for effective budget management. This...
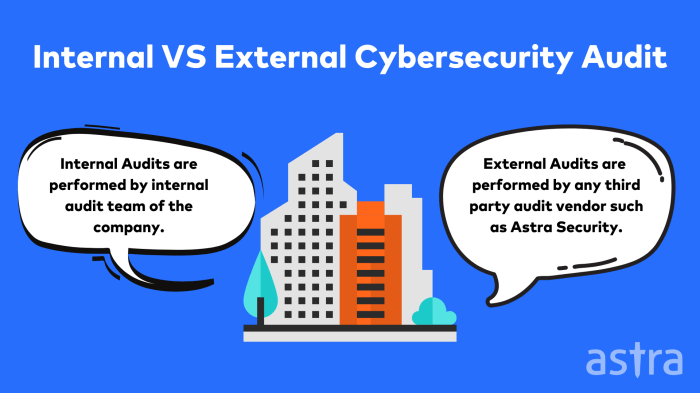
Navigating a cloud security audit can seem daunting, but this comprehensive guide provides a clear roadmap for preparation and success. The article me...
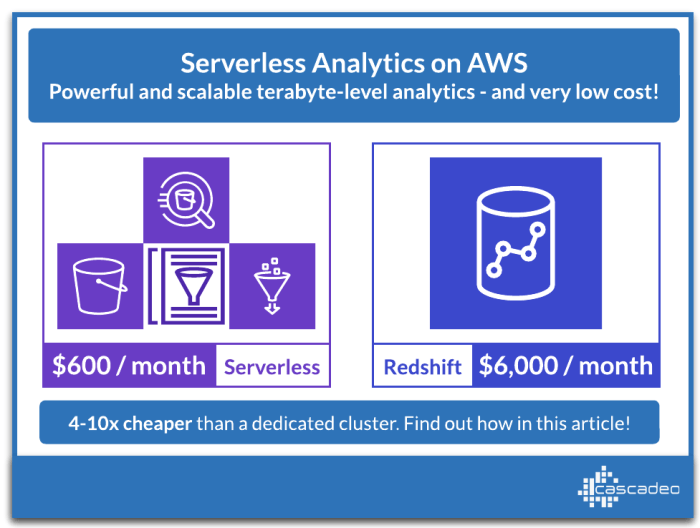
Serverless analytics provides significant advantages in scalability and cost-efficiency, but achieving peak performance requires targeted optimization...

This comprehensive guide to Cloud Identity and Access Management (IAM) explores core concepts, best practices, and emerging trends to secure your clou...
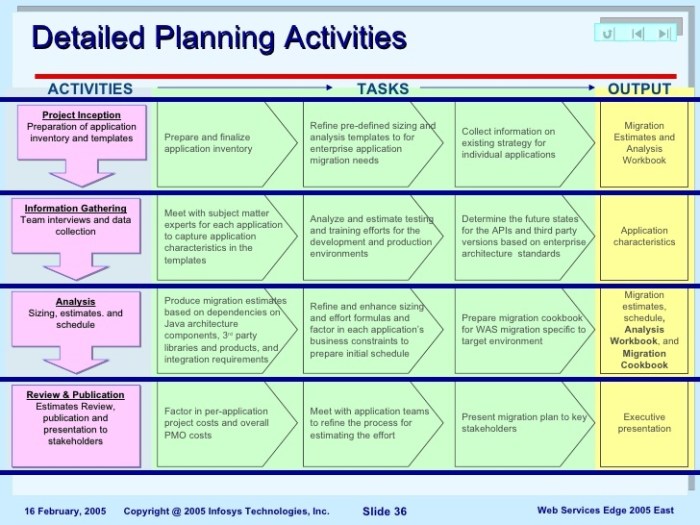
Data migration projects rely heavily on a well-defined final cutover plan, a crucial roadmap for transitioning from legacy systems to new ones. This p...
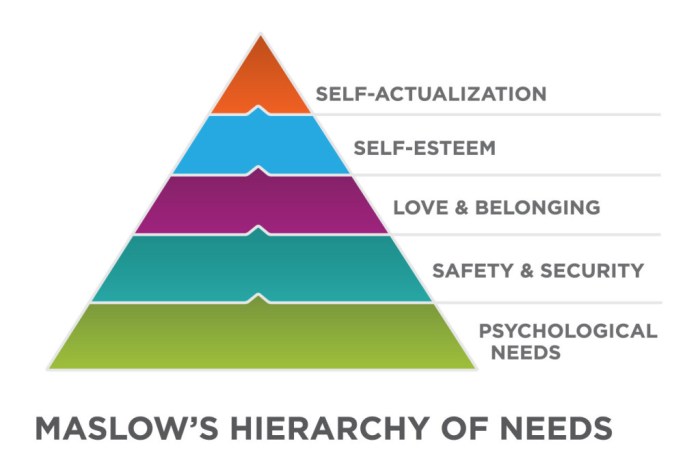
The increasing convergence of Internet of Things (IoT) devices and cloud services necessitates a thorough examination of the associated security risks...